Certificate Authority Templates. You also can tell AC to run a script when it connects to a community but the catch is the script isn’t included within the profile and instead you would possibly be required to place it on the machine with another technique. The similar goes for different social media and print design templates like postcards, business playing cards, e-mail headers, and Facebook adverts. The hidden SSID possibility tells ISE that it needs to actively probe for the SSID since the network isn’t going to be broadcasting itself. This free template displays a artistic and enjoyable design with hand drawn scribbles.
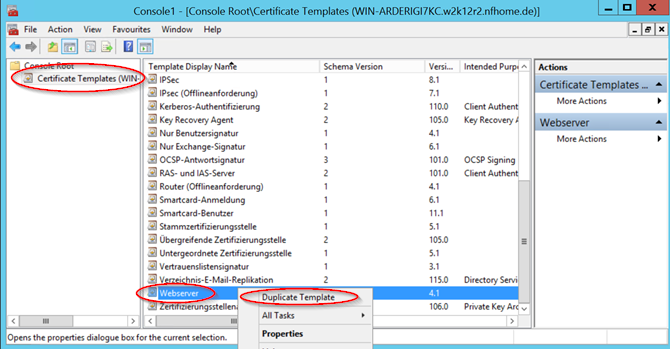
Sometimes, you can pick a structure, alter it and demand the blessing style-certificates in mass. As proven right here, the certutil -setCAtemplates command can both add templates (+Template name) or remove templates (-Template name). This offers a verify on the origin of software so that code management systems and end-users can ensure that the origin of the software is trusted.
Besides the CRL, they want to additionally implement the Online Certificate Status Protocol which is an alternative alternative to CRLs. For an outline of certificate templates, see Certificate templates. •If the person had not ever logged into the PC, they’d not be able to log in without connectivity to the area controller. Government Data storage, AI, and analytics options for presidency companies. Text field, enter VMware as the name of the model new template.
Acknowledgment to their tech-inspired designs, they’re a plentiful way to wean your kids off their electronics—at atomic quickly. Aspiring engineers, inventors, mathematicians, and added can analyze their adroitness with certainly one of these STEM creator books. Included are puzzles, patterns, and templates that children can ample out, or blush in, whereas acquirements added about their tailored area.

Because of the chronic shortages of cash of all kinds in the colonies, these cards were accepted readily by merchants and the public and circulated freely at face value. It was supposed to be purely a temporary expedient, and it was not until years later that its function as a medium of trade was recognized. The first issue of playing card money occurred during June 1685 and was redeemed three months later.
Issuing Good Card Certificates
The manufacturing of new physical money is normally the responsibility of the nationwide bank, or sometimes, the federal government’s treasury. Colonial powers consciously introduced fiat currencies backed by taxes (e.g., hut taxes or poll taxes) to mobilise economic resources of their new possessions, no less than as a transitional association. The objective of such taxes was later served by property taxes.
This template is identical to the OCSPSigningCertificate template with one difference. In this template, ACM Private CA passes further extensions from the certificates signing request into the certificates if the extensions usually are not specified in the template.
Certificate Authority Templates 6
▪Enrollment Agent Certificates derived from this template are used to request and problem other certificates from the enterprise CA on behalf of another entity. For instance, the net enrollment application makes use of these certificates to manage the certificate requests with the CA.
You can download pardon Certificate Authority Templates in your certificates. At that point, you just dependence to print it and get it marked or stepped for the credited acknowledgment. You can present certificates on your understudies who have competent essentially the most elevated score for this course.
Related Merchandise
Google Workspace Collaboration and productivity tools for enterprises. Productivity and Collaboration Change the greatest way teams work with solutions designed for humans and built for influence. Virtual Desktops Remote work options for desktops and functions (VDI & DaaS).
CA certificates include a critical Basic constraints extension with the CA area set to TRUE to designate that the certificate can be used to concern CA certificates. Extended key utilization just isn’t included, which prevents the CA certificate from getting used as a TLS client or server certificate.
Microsoft Windows Server 2008
In the Trusted Sites dialog box, click Add and Close. Now we’ll request a certificate for the branch workplace firewall. After we get hold of the certificate, we will copy the CA certificate into the machine’s Trusted Root Certification Authorities certificates store.

For example, customers utilizing Code Signing for AWS IoT can generate a code-signing certificate with ACM Private CA and import it to AWS Certificate Manager. For more information, see What Is Code Signing for AWS IoT? ACM Private CA makes use of configuration templates to issue each CA certificates and end-entity certificates.

We are validating independently when a user is authenticated to a website PC, and in addition when a site PC is authenticating without a person authenticated . Since we’re speaking about EAP-Chaining we’ll need to choose Machine and User Connection.

Choosing a CA that you can belief is important, as a outcome of your digital services and products and your end-user’s security is reliant upon the expertise your CA offers. Trusted CAs submit to regular audits by independent events, comply with trade guidelines and preserve finest practices to secure their infrastructure.
In a mannequin by Kiyotaki and Wright, an object with no intrinsic price can have value throughout trade in one of many Nash Equilibria. If the Storage Provider Certificate is still valid, however is coming near expiring, then renewing it is simple.

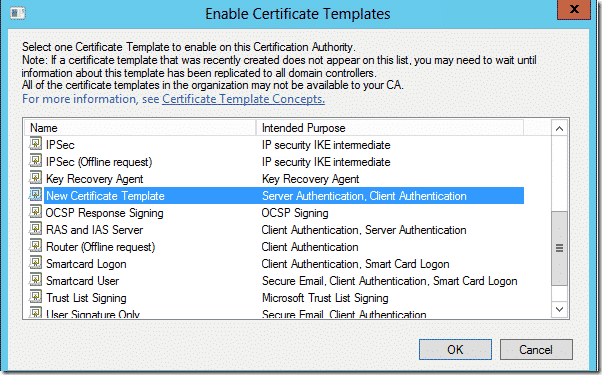
TheCertification Authority setting governs which Windows Server variations working the Certification Authority function will have the ability to use all CA-related settings on the certificates template. TheCertificate recipientsetting does the same for techniques that request a certificates from the CA. Note that the compatibility settings don’t have any impact on the systems that will communicate with licensed machines nor will they necessarily forestall a down-level system from having a certificates issued.
Download templates for gift certificate and give your good friend, relative, or significant different the present of doing a fun activity with you. Whether it is an award or present, Microsoft has a certificates template for nearly any occasion.

What could take a number of guys 2 hours or extra every to find is accessed in round 15 minutes on Experts Exchange. See if this resolution works for you by signing up for a 7 day free trial. Other “how-to” articles are launched within the Federated Authentication Service configuration and administration article.

With blank end-entity certificate templates, you’ll have the ability to problem end-entity certificates with solely X.509 Basic constraints current. This is the simplest end-entity certificate that ACM Private CA can issue, but it can be custom-made utilizing the API structure.

Makes the request to the SCEP server on the system’s behalf and then pushes the SCEP certificates to the device. Enables shopper computers to authenticate their identity to servers.
Certificate Authorities, or Certificate Authorities / CAs, concern Digital Certificates. Digital Certificates are verifiable small knowledge files that contain id credentials to help websites, people, and units symbolize their authentic online identity . On the member server that has Certificate Services installed, in the Certification Authority console, right-click Certificate Templates and click Manage to load the Certificate Templates console.

In Windows Server 2012, the capability of renewing a certificates with the identical key was launched. This performance will work when clients that beforehand received a template which are configured for renewal with the identical key try to renew it. Windows Server 2012 and Windows 8 can enforce certificates renewal with the identical key.

Under the Advanced settings area each enforce advanced 802.1x settings and enable Single Sign On. •Disable removable media access to make removal of key data instantly from a system more difficult.
▪EFS Recovery Agent Certificates of this kind permit information that have been encrypted with the EFS to be decrypted in order that the files can be utilized once more. EFS Recovery Agent certificates should be part of any catastrophe restoration plan when designing an EFS implementation. Enables you to suspend automated certificate issuance by choosing the CA certificates supervisor approval check box.

Data Cloud Alliance An initiative to make certain that world businesses have more seamless entry and insights into the info required for digital transformation. Database Migration Guides and instruments to simplify your database migration life cycle.

Shows the default permission degree for the Authenticated Users group. For a user to request a certificate, nonetheless, the user must have no less than the Enroll permission assigned to her or him for guide requests and the Autoenroll permission for automatic requests. Gives you the selection of obtaining topic name data from Active Directory or from the certificates request itself.
User V2 is the template we simply created for use for “soft” shopper certificates.The certificates services enrollment point on this example is configured for Username/Password authentication. Logon is completed with a test AD person account , who is a member of the GU-SEC-ADCS-Workgroup and licensed with the enroll permission. Such certificate in addition to the public/private key pair can be generated by everybody.

These forms of notes have been issued significantly in Pennsylvania, Virginia and Massachusetts. Such cash was offered at a reduction of silver, which the federal government would then spend, and would expire at a hard and fast date later.
We make it easy for everyone to create an exquisite, skilled net presence. Kids can use their acuteness and adroitness to physique bright 3D creations of their own design—including a box to authority Easter candy—with this 32-piece set of Magna-Tiles. It’s a fun method for them to advance algebraic and science skills while acquirements cooperation and teamwork.
Because every Windows PC is going only to dot1x authenticate with its computer credential always, it is inconceivable to apply community policy based on the person who is logged into the PC. ISE never actually learns who is logged into the system.

They regularly think about that they should structure the certificate and spend a fantastic settlement of cash to accumulate it. Notwithstanding, you don’t have to squander your cash on lavish structure. Actually, you possibly can purchase a good settlement of marginal greater than the online.

If company policy requires that different network entry coverage be applied based mostly on person safety group membership, computer-only authentication is generally not an option. The certificate objective can be encryption, signature, or signature and encryption. There can be an option to permit the export of the private key.

Disadvantages to this deployment are that at the time of this writing EAP-Chaining is a Cisco proprietary methodology that requires the AnyConnect NAM and is as such a Windows-only feature. If different platforms are required, OSX or some other mobile OS, one other methodology would have to be used.
[ssba-buttons]