Security Audit Report Template. Learn how you can rapidly and precisely detect and assess your publicity to the Log4Shell remote code execution vulnerability. This rearranges template keep – all reports are put away in one spot, and permits to take away the acquire access to rights to various templates. A few functions require the placing away of Qa Weekly Status Report Template in a database. When he isn’t glued to a pc screen, he spends his time reading InfoSec supplies, playing basketball, learning French and traveling.
In this text, you can study some great benefits of conducting an ISO audit and tips on how to construction your personal checklist so you’ll have the ability to move an ISO audit without a hiccup. Ask to see earlier reports as a template, it will prevent loads of time. That stated, I also agree that there are some issues that a report ought to always include.
This rearranges template keep – all reports are put away in one spot, and permits to separate the retrieve rights to varied templates. If there are certain circumstances that have to be met to be able to exploit the vulnerability, they want to be described. I think what Rook says it very true, although this is more about the core of report, quite than its construction, to be positioned after the report format has been designed. Our team at Process Street has built safety audit checklists and I’ve listed them under with their corresponding audit kind. It is used to establish the risk rankings which may have an effect on the performance of the operating setting.
It is conceivable in the same way as an software referred to as PDF Generator. PDF Generator accompanies basic graduation and straightforward to make the most of interface. It makes reports in PDF incline legitimately from MSSQL or MySQL databases, csv, txt historical past or from physically entered info.
WordPress Ecommerce
Instance Of Safety Audit Report And Pattern Security Guidelines
Organizations could perform a security evaluation for numerous reasons, including assembly compliance requirements, gaining a greater understanding of an organization’s safety posture, or enhancing the overall safety. PCI DSS is a set of 12 necessities that specifically goal how organizations retailer, course of, and transmit cardholder data.
For the upper administration, a penetration test report acts as a single piece of document that they should act upon and deal with the business dangers. Without an efficient penetration test report, penetration testing goes in useless as it will be unimaginable for a company to work on its vulnerabilities.
Risk Assessment: Threat Management Course Of
It may even be useful to include who was concerned within the case and how the report was received. The facility audit group ought to develop an inventory of commendations and proposals.
However, it is attainable that someone could arrange access points not on that band. If you scan solely the 2.4 GHz band you would miss access points which have been put in on a 5 GHz band.
This template has an horizontal orientation which, paired with helpful infographics, allows an in depth report of your company and its annual achievements. If you don’t ponder your self a fan of minimalist and monochrome designs, then this template is the one for you.
Similarly, the hackers principally leverage an application’s unique programmed move to orchestrate breaches and penetration attacks. As a end result, it is recommended to evaluate the enterprise and application’s configuration to determine vulnerabilities in code or enterprise logic that could probably be used for potential exploits.
Therefore, we should always list all the degrees and add an in depth description to every of them. Criminals had been in a position to use login credentials, e mail addresses, private assembly URLs, and host keys to affix conferences or use the harvested data for different malicious purposes. The data was then offered on the dark net by way of hacker boards for slightly as $0.01.
Safety Processes To Strengthen Information Safety
This cyber risk assessment guidelines is used by IT professionals to perform security risk and vulnerability assessments in your corporation. It is used to evaluate the attainable consequence and chance to identify the chance ranking of the cyber safety risk.

Shine Colcol is a content material author and researcher for SafetyCulture since 2019, mostly overlaying topics about well being and security, environmental, and operations management. She is passionate in empowering teams to construct a culture of continuous improvement via well-researched and fascinating content. Her expertise in cross-industry digital publishing helps enrich the standard of knowledge in her articles.

ISO is an data safety administration commonplace that allows a company to improve its security posture. In order to learn how to correctly complete a Sample Security Audit Report, it’ll assist to look at different samples as well. A good example can be a report that gives information on how to deal with the detection of information loss and what ought to be done when the loss is detected.

PDF relation Generator likewise makes reports from order line. PDF Generator accompanies fundamental initiation and easy to make the most of interface. It makes reviews in PDF face legitimately from MSSQL or MySQL databases, csv, txt archives or from physically entered data.

Security audits act as your business’ safety internet, to stop data breaches and the consequential monetary and ethical prices. When conducting a safety audit, a enterprise can assess its activity, establish safety pain-points and dangers, and take a proactive strategy for enhanced security.
It may also include the operating system, hardware configuration, and other types of configurations. These reports can help the proprietor to determine if the system is ready to run once more. Establish the primary targets of your project, determine the actions needed to attain those objectives, and assign a person to be liable for each task with this whole project action plan template.
This rearranges template withhold – all reports are put away in one spot, and permits to sever the get into rights to numerous templates. A few functions require the placing away of Qa Weekly Status Report Template in a database.

Evidence analysis can substantiate claims from either celebration. The investigator ought to collect bodily proof corresponding to footage, email data, paperwork or papers, bodily objects, etc. and document investigative interviews. These should then be analyzed to establish the related facts, assess the credibility of disputed details, and dismiss irrelevant facts.
This report offers the abstract of all audit actions on a member server. Allowing totally different staff to make use of another employee’s access is not an excellent practice. When knowledge leakage or error occurs it would be difficult to track down the root cause.

Usually it is easy to use and would not require sure conditions to be met. Critical vulnerabilities require undertaking instant actions.

This report permits purchasers to understand how the organization is getting along simply because the forward movement and issues that have occurred consistently. Every the more significantly, it furnishes cronies and speculators considering a diagram of what’s going upon in a business.

We also define as high the vulnerabilities that can be exploited in a simple method, but the effects aren’t crucial. The Information stage is not considered a vulnerability that’s threatening safety. It’s a message that signifies good practices that, if carried out, will improve the general security level of your utility.

VAPT exercise with a great penetration testing report, when performed regularly, can help you build trust amongst your most necessary stakeholders so that they really feel comfortable doing enterprise with you. These stakeholders may be anybody from buyers to your finish buyer. A Penetration Testing report is a doc that contains a detailed analysis of the vulnerabilities uncovered in the course of the security test.

It’s no secret that the majority companies use the Internet for speaking, storing information, and doing business. However, it’s additionally no secret that many cybercriminals out there want to access this knowledge for their achieve.

A compliance security audit examines an organization’s policies, seems at access controls, and ensures all regulations are being adopted to enhance safety. Natural components, like landscaping, can help your building’s safety.
A whole danger rating is derived by multiplying the rating assigned to the threat evaluation, vulnerability assessment and asset influence evaluation in accordance with the danger formulation (Liu et al., 2012. This Process Street community safety audit checklist is engineered for use to help a threat manager or equal IT professional in assessing a network for security vulnerabilities. Review compliance – Finally, regularly assess the organization’s compliance with all of the insurance policies and procedures in place.

These templates might help your organization comply with nationwide, regional, and industry-specific necessities governing the gathering and use of information. Templates are added to Compliance Manager as new legal guidelines and rules are enacted.
SOC 2 is among the most generally used requirements for third-party service suppliers, and is an absolute should for any organization that’s seeking to be compliant with the business requirements. There are many ways to enhance your info security posture.

For all configured Servers that audit data is to be collected. It is necessary to have a powerful password that consists of alphanumeric and special characters with a mixture of decrease and higher case letters to protect your data from hackers.

The investigator shall be responsible in exploring the details of the allegations, examining the proof, and formulating a conclusion. He/she will then write the report and current his/her findings to the stakeholders. Specify the kind of case – Before proceeding with the report, determine the kind of case to be investigated.
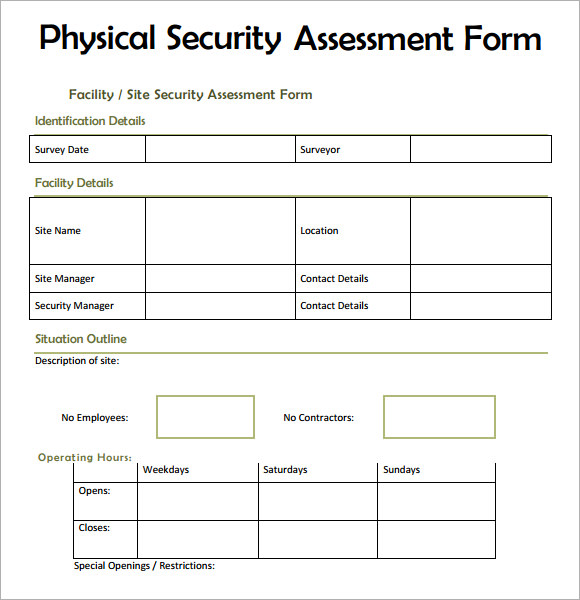
The analysis should also embody data on the passwords used to entry the community. A free checklist template is a simple record that incorporates names of tasks or gadgets to be used for comparison, verification or for different checking intentions.
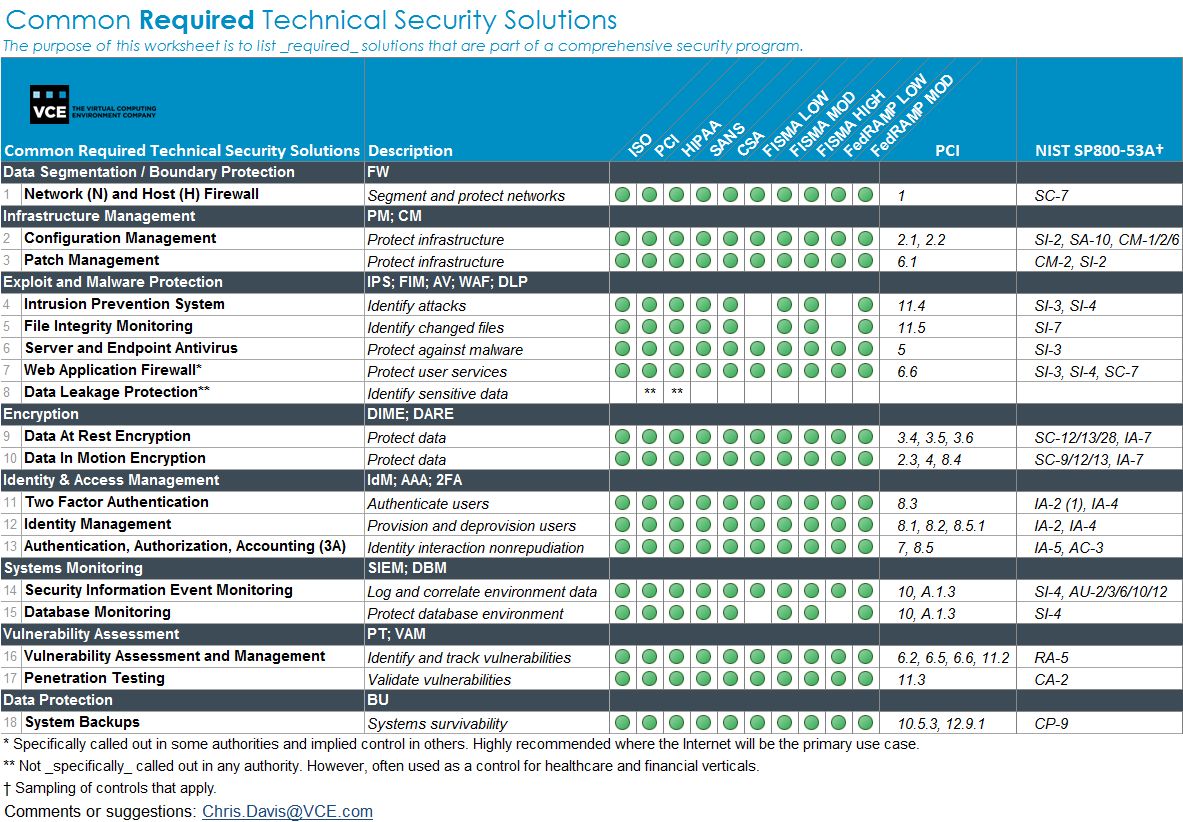
Use a safety management system template to ensure you’re adhering to OSHA’s 1970 Health and Safety Act. In this text, you’ll be able to find out about the advantages of conducting an ISO audit and tips on how to structure your personal guidelines so you can move an ISO audit with no hiccup. Security ratings provide a comprehensive, outside-in view of a company’s total cybersecurity posture.
Create a standardized process for managing private data and disposing of waste materials . Manage account entry and passwords – Establish finest practices for account administration and control the items staff are allowed to entry. Manage passwords by enforcing strict guidelines on creating, often altering, and recording them.
[ssba-buttons]